Introduction
Imagine a lock so secure… no computer on Earth could crack it in a million years. That’s the power behind every Bitcoin transaction you make. At the heart of it exists something called SHA-256.
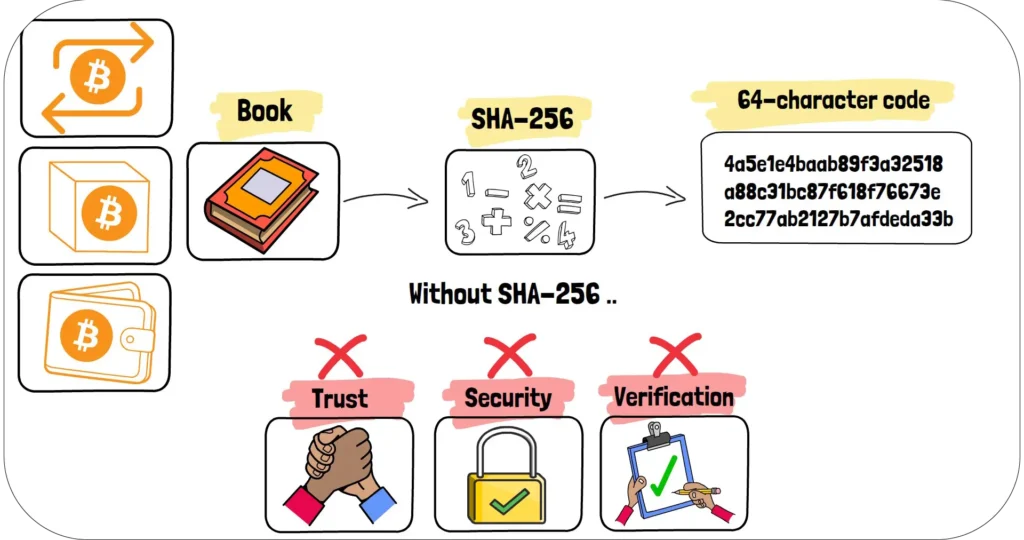
SHA-256 is Bitcoin’s digital fingerprint maker. Every piece of data that enters the Bitcoin network—every transaction, every block, every detail—gets processed through mathematics. It takes any input, let’s say an entire book and transforms it into a unique 64-character code. Always 64 characters and always different for different inputs.

Without it, there would be no trust, no security, no way to verify that your digital money is actually yours. It’s what allows everyone around the world to transact without needing banks or governments to vouch for them.
In this video I will attempt to explain what SHA-256 is, how it works, why it’s important to Bitcoin’s success and more. All am asking from you is to subscribe and share this video as it took me a lot of reading and countless hours to make.
Purpose in Bitcoin
Before Bitcoin, digital transactions required banks to verify and approve every payment. Someone had to act as the middleman, keeping track of who owned what. But Bitcoin completely changed this model. Instead of relying on institutions, it uses mathematics—specifically, the SHA-256 hash function—to create an unbreakable chain of trust.

Think of SHA-256 as the digital equivalent of a wax seal on an ancient letter. Just as a broken seal would reveal tampering, any change to Bitcoin data—even a single character—produces a completely different hash. This makes fraud virtually impossible. If someone tries to change a transaction amount from $10 to $1,000, the hash would change entirely, immediately notifying the network to the tampering attempt.

But SHA-256 does more than just detect fraud. It’s the foundation of Bitcoin’s mining process—the mechanism that adds new transactions to the blockchain and releases new bitcoins into circulation. Miners compete to solve complex mathematical puzzles that rely entirely on SHA-256 computations. The first miner to find the correct solution gets to add the next block to the chain and earn the block reward.
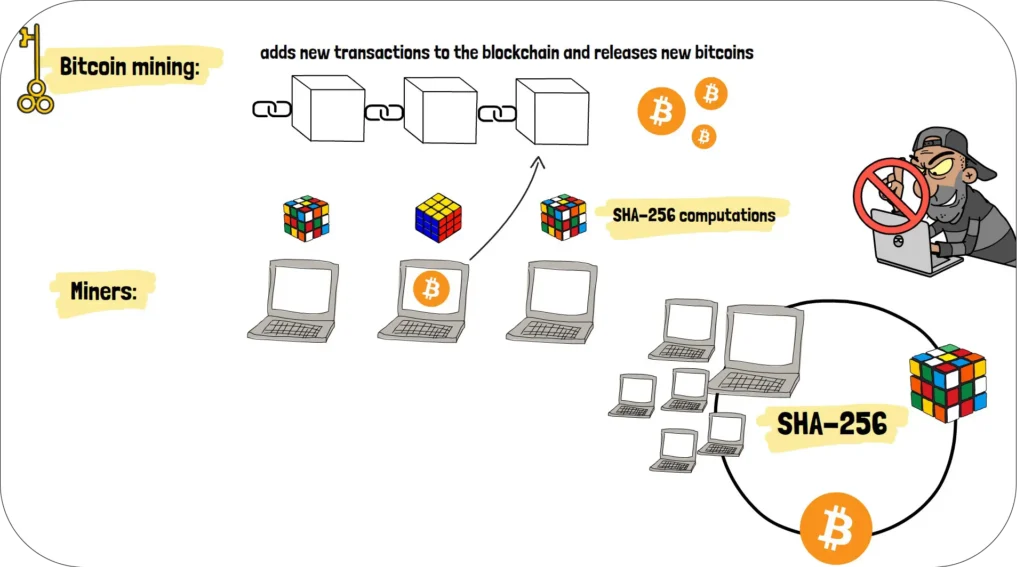
This elegant system creates a self-reinforcing cycle of security. The more miners participate, the more secure the network becomes. And it all starts with SHA-256—the unsung hero keeping your Bitcoin safe.
Key Components
Let’s break down SHA-256 into its essential parts. Don’t worry—we’ll keep this as simple as possible.
First, there’s the input. This can be literally anything: a transaction record, a block of data, even this entire manuscript. SHA-256 doesn’t care what you feed it. It could be a single word or a massive database. The function treats everything the same way.
Next comes the magical transformation process. Think of SHA-256 as the ultimate blender. You pour in your ingredients—your data—and it scrambles everything into a perfectly uniform smoothie. But unlike a real blender, this digital version always produces exactly the same result for the same input. Feed it the word “Bitcoin” a thousand times, and you’ll get the same hash every single time.
The output is where things get interesting. No matter what you put in, SHA-256 always spits out exactly 64 characters. These aren’t random letters and numbers—they’re hexadecimal characters, meaning they only use digits 0-9 and letters A-F. A typical Bitcoin transaction hash might look like this: e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
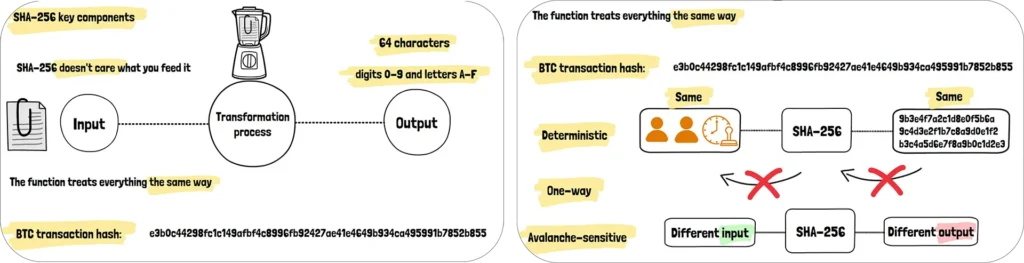
But here’s the truly remarkable part: SHA-256 has three critical properties that make it perfect for Bitcoin. First, it’s deterministic—same input always produces the same output. Second, it’s one-way—you can’t work backwards from the hash to discover the original data. And third, it’s avalanche-sensitive—change even one tiny bit of input, and the entire output changes dramatically.
There’s also something called a nonce in Bitcoin mining. Don’t let the fancy name intimidate you—it’s just a number that miners guess repeatedly until they find one that produces a hash meeting specific criteria. Think of it as a lottery ticket number that miners keep changing until they win.
How It Works
Now let’s walk through exactly how SHA-256 works its magic. Picture a massive, incredibly sophisticated factory where data goes in one end and comes out completely transformed on the other side.
When you initiate a Bitcoin transaction, the network takes all your transaction details—the amount, the sender, the receiver, timestamps—and feeds them into the SHA-256 function. Inside this digital factory, your data goes through a series of precise mathematical operations. The function breaks your input into chunks, performs complex bit manipulations, and runs everything through multiple rounds of calculations.
Here’s where it gets fascinating: the process involves exactly 64 rounds of computation. Each round takes the data through specific mathematical operations—additions, rotations, and logical functions that have names like AND, OR, and XOR. It’s like passing your data through 64 different specialized machines, each one scrambling it a little more.
The SHA-256 algorithm uses eight initial hash values, kind of like starter ingredients in a recipe. These values are the first 32 bits of the fractional parts of the square roots of the first eight prime numbers. This isn’t random—it’s a carefully chosen mathematical foundation that ensures the function’s security and reliability.
During each round, the algorithm processes the data in 512-bit chunks. If your input isn’t a perfect multiple of 512 bits, the function automatically adds padding to fill the gap. This ensures consistent processing regardless of input size.
The final result? After all 64 rounds of computation, you get your unique 256-bit hash—that’s where the “256” in SHA-256 comes from. This hash serves as an unbreakable digital fingerprint for whatever data you put in. Change even one character in your original input, and the entire hash transforms into something completely different.
Implementation in Bitcoin
So how does Bitcoin actually use SHA-256 in practice? It’s implemented in three crucial ways that work together to create the world’s most secure digital currency system.
First, SHA-256 secures individual transactions. Every time you send Bitcoin, the network creates a hash of your transaction details. This hash becomes part of the permanent record, making it impossible for anyone to alter the transaction later. It’s like having a tamper-proof seal on every digital payment.
Second, SHA-256 creates the blockchain structure itself. Each block in the Bitcoin blockchain contains a hash of the previous block, creating an unbreakable chain. Think of it like a digital DNA strand—each block inherits genetic information from its parent, and any attempt to alter the past would break the entire chain. This is why Bitcoin’s history is considered immutable.
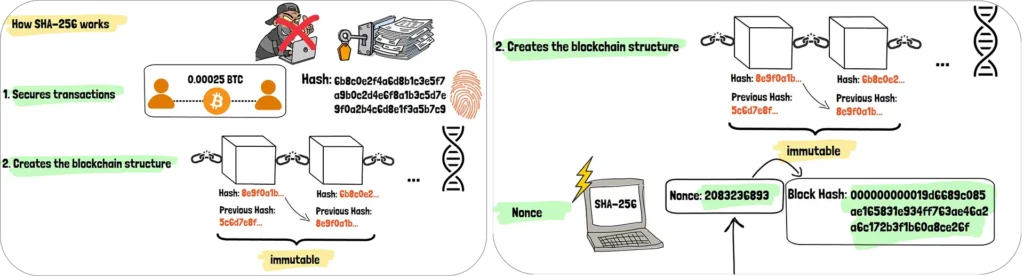
The third implementation is in mining—the process that keeps Bitcoin running. Miners use SHA-256 to compete in solving complex puzzles. They take a block of pending transactions, add a random number called a nonce, and run everything through SHA-256. The goal is to find a hash that starts with a specific number of zeros. The current Bitcoin network requires hashes to start with approximately 19 zeros—a task so difficult it requires enormous computational power.
Bitcoin also uses SHA-256 in something called Merkle trees. These are like digital family trees that organize all transactions in a block. Each transaction gets hashed, then pairs of hashes get hashed together, creating a tree structure that leads to a single root hash. This clever system allows anyone to verify a transaction’s inclusion in a block without downloading the entire blockchain.
You can see SHA-256 in action using block explorers like Blockchain.com or Blockchair. Every transaction, every block, every piece of Bitcoin data displays its unique SHA-256 hash. It’s like having a window into Bitcoin’s mathematical soul.
Challenges and Limitations
While SHA-256 is remarkably secure, it’s not without challenges. The most obvious issue is energy consumption. Bitcoin’s network currently processes approximately 34 billion billion SHA-256 hashes per second
—that’s more computational power than the world’s most powerful supercomputers. This incredible hash rate requires massive amounts of electricity, leading to ongoing environmental concerns.
The security that makes SHA-256 so valuable also makes it slow. Each hash computation takes time, and Bitcoin’s design intentionally limits block creation to approximately every 10 minutes. This creates a fundamental trade-off: security versus speed. While traditional payment systems can process thousands of transactions per second, Bitcoin’s base layer handles only about 7 transactions per second.
There’s also the looming threat of quantum computing. While current quantum computers pose no threat to SHA-256, future quantum systems might be able to break cryptographic hash functions. However, this risk is still theoretical—experts estimate it would take quantum computers with millions of stable qubits to threaten SHA-256, far beyond current technology.
Another challenge is the fixed nature of the algorithm. SHA-256 was designed in 2001, and while it remains secure today, cryptographic standards evolve. The National Institute of Standards and Technology (NIST) has already begun preparing for post-quantum cryptography, though widespread adoption is still years away.
Mining centralization presents another concern. While SHA-256 itself is decentralized, mining operations have become increasingly concentrated in large pools and specialized facilities. This doesn’t compromise the algorithm’s security, but it does raise questions about Bitcoin’s overall decentralization.
Despite these challenges, SHA-256 remains incredibly robust. It’s been battle-tested for over two decades, withstood countless attempts to break it, and continues to secure trillions of dollars in value. The limitations are real, but they’re being actively addressed through innovations like the Lightning Network, which enables faster payments while maintaining SHA-256’s security guarantees.
Best Practices for Understanding
Ready to dive deeper into SHA-256? Here are some hands-on ways to explore this fascinating technology and build your understanding from the ground up.
Start with online SHA-256 tools. Websites like SHA256calc.com or online converters let you input any text and see the resulting hash instantly. Try typing “Bitcoin” and note the output. Now try “bitcoin” (lowercase) and watch how the entire hash changes. This simple experiment demonstrates the avalanche effect—one small change creates a completely different result.
Next, explore Bitcoin block explorers. Sites like Blockchain.com or Blockchair show real SHA-256 hashes in action. Look up any Bitcoin transaction and you’ll see its unique hash. Click on the block containing that transaction to see how all transaction hashes combine into a single block hash. It’s like watching Bitcoin’s mathematical heartbeat in real-time.
Read the original Bitcoin whitepaper by Satoshi Nakamoto. While technical, it’s surprisingly accessible and explains how SHA-256 fits into Bitcoin’s overall design. Don’t worry if you don’t understand everything—each reading reveals new insights.
For programming enthusiasts, try implementing simple hash functions yourself. Languages like Python have built-in SHA-256 libraries. Writing a few lines of code to hash strings helps demystify the process and builds intuitive understanding.
Join Bitcoin communities and forums. Platforms like Reddit’s r/Bitcoin or Bitcoin.org’s community section are great places to ask questions and learn from others. Many experienced users are happy to explain concepts to newcomers.
Remember, understanding SHA-256 is a journey, not a destination. Start with the basics, experiment freely, and don’t be afraid to make mistakes. Every expert was once a beginner who kept asking questions.
Real-World Impact
SHA-256’s influence extends far beyond abstract mathematics—it directly affects every person who interacts with Bitcoin. Let’s explore how this powerful algorithm shapes the real-world experience of different users.
For everyday Bitcoin users, SHA-256 provides invisible but crucial security. Every time you check your wallet balance, send a payment, or receive Bitcoin, you’re relying on SHA-256 to ensure the integrity of your transactions. It’s like having a personal security guard who never sleeps, constantly verifying that your digital money is exactly where it should be.
Miners experience SHA-256 most directly. Picture a miner in a warehouse filled with humming machines, each one frantically computing millions of hashes per second. They’re racing against miners worldwide, all trying to solve the same mathematical puzzle. The winner—the first to find a hash with enough leading zeros—gets to add the next block to the blockchain and earn the block reward. Currently, that reward is 3.125 bitcoins, worth tens of thousands of dollars.
For developers building Bitcoin applications, SHA-256 is both a tool and a constraint. They must design systems that work within Bitcoin’s security model while providing user-friendly experiences. Wallet developers, for instance, use SHA-256 to generate secure private keys and verify transaction authenticity. Exchange developers rely on it to ensure deposit and withdrawal accuracy.
Merchants accepting Bitcoin benefit from SHA-256’s immutability. Once a customer’s payment receives enough confirmations—typically 6 blocks—the transaction becomes practically irreversible. This eliminates the chargeback fraud that plagues traditional payment systems, giving merchants confidence in Bitcoin payments.
However, SHA-256 also creates challenges. The energy-intensive mining process has sparked debates about Bitcoin’s environmental impact. Some businesses avoid Bitcoin due to these concerns, while others embrace it as a driver of renewable energy adoption. The slow transaction processing also means Bitcoin isn’t suitable for small, instant payments like buying coffee—though solutions like the Lightning Network are addressing this limitation.
The global nature of SHA-256 creates interesting dynamics. A miner in China competes with miners in Texas, Iceland, and Kazakhstan, all solving the same mathematical problem. This creates a truly global security network where no single entity can control Bitcoin’s operation.
Current Developments and Future Outlook
The world of cryptographic hash functions is constantly evolving, and SHA-256’s future within Bitcoin continues to develop in exciting ways. While the algorithm itself remains unchanged and secure, the ecosystem around it is buzzing with innovation.
One of the most promising developments is the Lightning Network, which enables instant Bitcoin transactions while maintaining SHA-256’s security guarantees. Instead of putting every transaction directly on the blockchain, Lightning creates payment channels that settle using SHA-256-secured transactions. This allows for millions of transactions per second while reducing the computational load on the main network.
Researchers are also exploring more efficient mining technologies. New ASIC (Application-Specific Integrated Circuit) designs continue to improve the energy efficiency of SHA-256 computations. Some mining operations are experimenting with immersion cooling and renewable energy sources to reduce environmental impact while maintaining security.
The development of quantum-resistant cryptography is another area of active research. While quantum computers don’t currently threaten SHA-256, organizations like NIST are preparing for future scenarios. The Bitcoin community is monitoring these developments closely, ready to upgrade if necessary while maintaining backward compatibility.
Mining pool protocols are evolving to become more decentralized and efficient. Technologies like Stratum V2 give individual miners more control over which transactions to include in blocks, potentially reducing centralization concerns while maintaining SHA-256’s security properties.
Interestingly, researchers are finding new applications for Bitcoin’s massive SHA-256 computational power. Some propose using the network for distributed computing tasks like protein folding or climate modeling, potentially making the energy expenditure serve dual purposes.
The future looks bright for SHA-256 in Bitcoin. The algorithm has proven remarkably resilient, withstanding decades of attempted attacks and analysis. As Bitcoin continues to mature, SHA-256 remains its unshakeable foundation—a digital bedrock that grows stronger with each passing block.
Conclusion
We’ve journeyed through the fascinating world of SHA-256, from its basic principles to its profound impact on Bitcoin and beyond. This remarkable algorithm—transforming any input into a unique 64-character fingerprint—serves as the unbreakable foundation of digital money.
Remember the key insights: SHA-256 creates trust in a trustless system, enables secure mining competition, and provides the mathematical certainty that makes Bitcoin possible. It’s simultaneously simple in concept and incredibly sophisticated in implementation. Every Bitcoin transaction, every block, every aspect of the network depends on this cryptographic marvel.
While challenges like energy consumption and quantum computing concerns exist, SHA-256 continues to prove its worth. It’s been battle-tested for over two decades, securing trillions of dollars in value and enabling financial freedom for millions of people worldwide.
The next time you send Bitcoin, check your wallet, or read about mining, remember that SHA-256 is working tirelessly behind the scenes. It’s the invisible guardian of your digital wealth, the mathematical proof that decentralized money really works.
Ready to explore further? Try experimenting with a SHA-256 calculator, explore a block explorer, or dive into the Bitcoin whitepaper. The deeper you dig, the more you’ll appreciate the elegant simplicity of this world-changing technology.
Bitcoin’s future—and SHA-256’s continued role in it—has never looked brighter. Welcome to the future of money, secured by mathematics.